Penetration Testing

Unleash the Power of Security: Expert Penetration Testing Services
We understand the critical importance of safeguarding your digital assets against potential cyber threats. With the rapidly evolving landscape of cybercrime, it has become imperative for organizations to proactively identify and address vulnerabilities in their systems and networks.


Our Approach
Our team of highly skilled penetration testers emulates real-world cyber attacks to uncover vulnerabilities, weaknesses, and potential entry points that malicious actors could exploit.
Comprehensive Assessment
Methodical Testing
Targeted Exploitation
Reporting and Recommendations

Range of Our Services
Our team of skilled penetration testers combines technical expertise with industry best practices to provide you with a thorough assessment of your digital infrastructure.

Network Security
Penetration Testing
We Identify vulnerabilities in your network infrastructure, including routers, switches, firewalls, and wireless networks. Test for weak or misconfigured network security controls.
Mobile Application
Penetration Testing
We Assess the security of your mobile applications on various platforms (iOS, Android, etc.). Identify vulnerabilities specific to mobile app development, including insecure data storage, weak authentication, and inadequate encryption.


Web Application
Penetration Testing
We Evaluate the security of your web applications, including websites, portals, and e-commerce platforms. Identify common vulnerabilities such as injection flaws, cross-site scripting (XSS), and authentication issues. Assess the effectiveness of session management and access controls.
Red Team
Penetration Testing
We Conduct comprehensive, multi-faceted attacks to simulate real-world cyber threats. Test the effectiveness of your organization’s overall security posture. Identify vulnerabilities across multiple layers, including technical, physical, and social engineering.



Benefits With Our Service
Tailored Approach
Our penetration testing services are tailored to your specific needs, ensuring that we address the areas of greatest concern to your business.
Cutting-Edge Tools and Techniques
We leverage the latest tools, techniques, and methodologies to uncover even the most hidden vulnerabilities.
Confidentiality and Compliance
We prioritize the confidentiality of your data and adhere to strict data protection and privacy regulations. You can trust us to handle your sensitive information with the utmost care and professionalism.
Continued Support
Our relationship with you doesn’t end with the penetration testing engagement. We are committed to providing ongoing support, guidance, and assistance to help you address any security concerns that may arise in the future.

Our Clients

Why Choose Us?


Certified Info Security Auditor
We're CERT - IN empanelled, which has meant that the biggest public and private enterprises have put their trust in us.

Reliability
We are the 6th company to get empanelled with government bodies like CERT-In & STQC which are recognised and respected by industry professional and organisations.
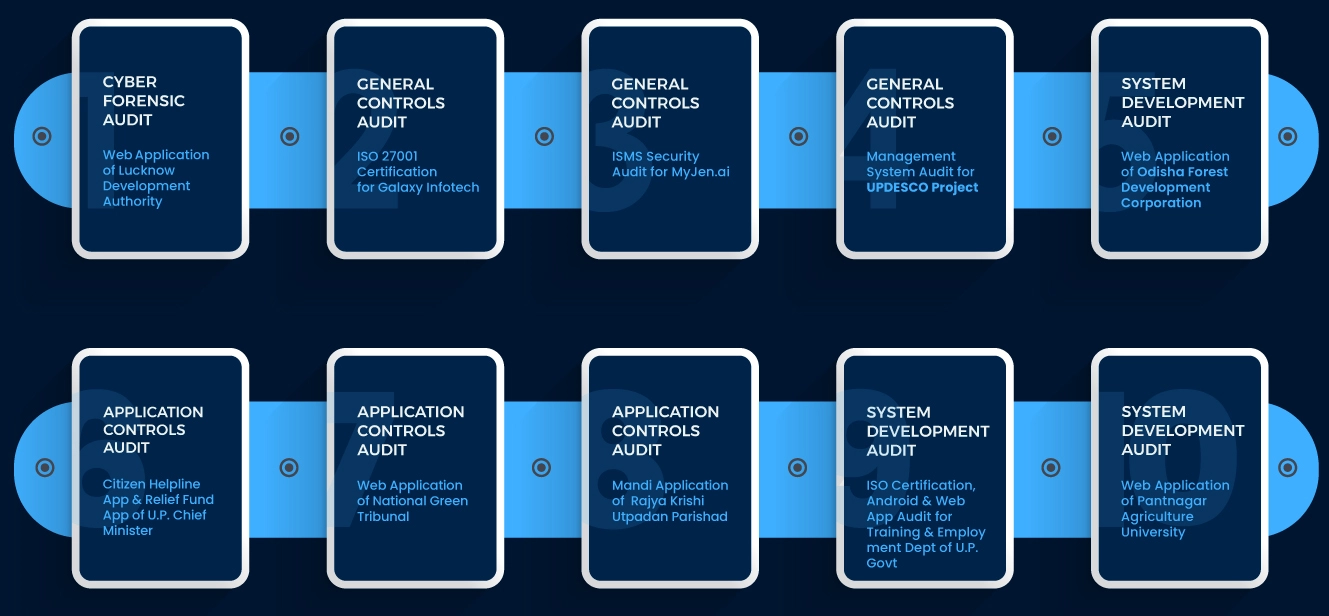
Projects We Delivered














Frequently Asked Questions
What happens after the Penetration Testing is completed?
After the Penetration Testing is completed, you will receive a detailed report outlining the vulnerabilities discovered, their potential impact, and recommended remediation actions. Our team will be available to provide guidance and support in addressing the identified security issues.
How long does a Penetration Testing engagement take?
The duration of a Penetration Testing engagement depends on the scope and complexity of the assessment. It can range from a few days to several weeks, including the planning, testing, and reporting phases. The timeframe will be discussed and agreed upon before the engagement begins.
How confidential is my data during the Penetration Testing process?
We prioritize the confidentiality and security of your data throughout the Penetration Testing process. Our team follows strict data protection and privacy policies. Any data obtained during the assessment is handled with utmost care and is only used for the purposes of the engagement.
Can you assist with remediation after Penetration Testing?
Yes, we provide comprehensive support during the remediation process. Our team can guide you through the recommended remediation actions, assist in implementing security measures, and provide ongoing support to strengthen your security defenses.


